Security outlook after Bitcoin halving: 51% attack is no longer the real risk

Bitcoin security outlook
The mechanism of the crypto asset (virtual currency) Bitcoin (BTC) is that new coins are issued in each block due to a protocol that has been incorporated since its creation. The issuance rate decreases each time.
This issuance schedule is designed to act as an incentive, or reward, for block production, and to continue decreasing until a cap of 21 million BTC is reached. And when that time comes, Bitcoin’s security will shift from traditional subsidies to user fees.
The risk of attack facing the Bitcoin blockchain network has always been a source of concern among the community. In particular, there is much debate as to whether Bitcoin can withstand the threat of a 51% attack even after reaching the 21 million BTC limit.
A 51% attack is the possibility of one entity gaining control of the majority of the mining hashrate and maliciously altering the ledger. In the case of Bitcoin, the biggest cost driver of this attack is the purchase of ASICs.
A research report published on February 15, 2024 suggests that a 51% attack on Bitcoin has become economically impossible. This study provides the first empirical evidence of Nash equilibrium in Bitcoin. In other words, miners decide it is more profitable to mine blocks honestly, and users choose to trust the network and make transactions.
Lucas Nuzzi, head of R&D at Coin Metrics, and his co-authors used a new model called Total Cost of Attack (TCA) to simulate the cost-effectiveness of these attacks. The attack on Bitcoin took into account the price of 51% of the ASICs active on the network and the power needed to operate them.
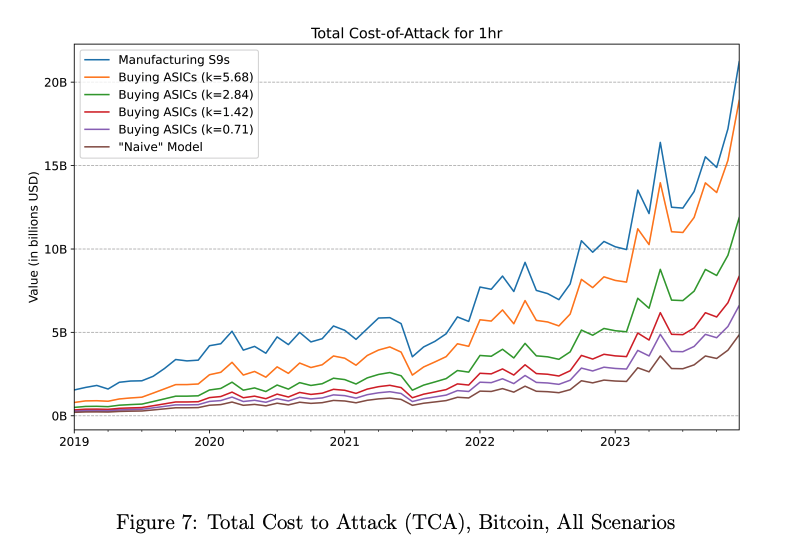
Bitcoin Total Cost of Attack (TCA), Source: Breaking BF
Based on ASIC market data, the cost of purchasing a 51% ASIC ranges from $5 billion (latest models with supply issues) to approximately $20 billion (S9 model), including the most profitable double-spending scenario. It is estimated that it will not be too much.
Importantly, there is no way to profit from attacking Bitcoin. The profits from actions such as double-spending, blockchain restructuring, and selfish mining cannot outweigh the costs of attacks.
Principle of miner operation
The research also shows that user fees are seen by Bitcoin miners as more than just a short-term source of income. Fees play an important role in encouraging miners to invest in the network and maintaining the security and stability of the entire Bitcoin ecosystem.
What is user fee?
A fee that users pay directly to miners to ensure that their transactions are added to the block with priority.
Historical statistics show that the level of fees does not directly correlate with the security of the network, and that the security of the Bitcoin network remains strong even with low fees. This confirms that miners are motivated to continue contributing to the network in anticipation of future value increases.
This is because even if miners speculatively deploy hashrate in anticipation of a high-fee cycle, it may take some time for that hashrate to actually come online, and market conditions may have changed. There is. Such a principle makes the relationship between fees and network security unpredictable.
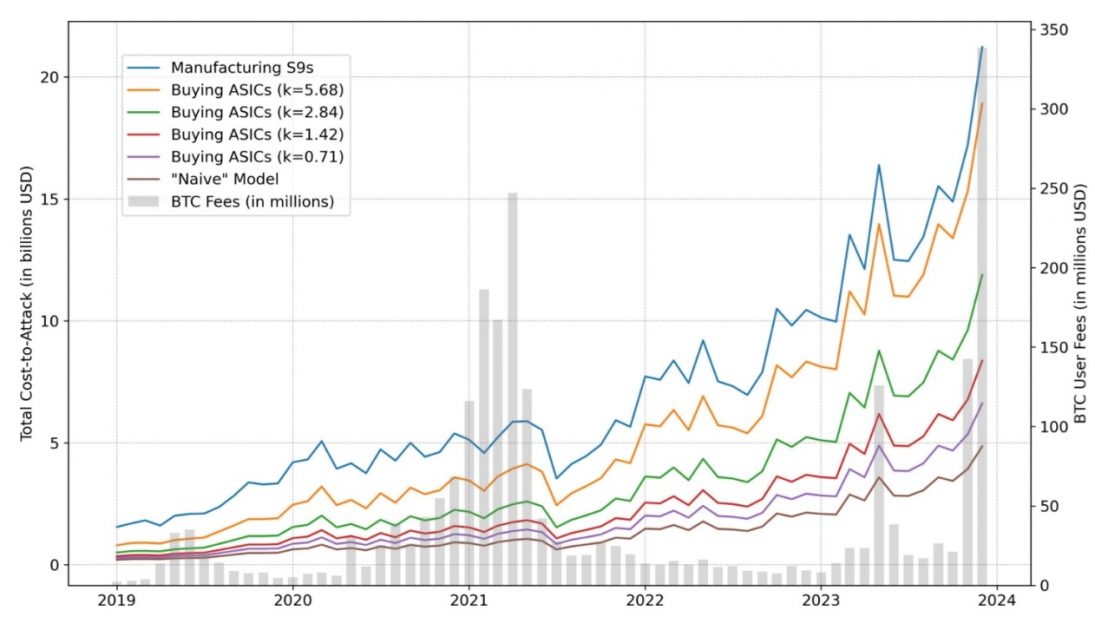
Comparison of Bitcoin fees (monthly) and total attack cost (TCA) Source: Breaking BFT
Furthermore, analysis of trends in wallets that manage newly issued coins shows that miners are speculators and are accumulating Bitcoin in anticipation of a future bull market. The diagram below shows that miners behave (accumulate and sell) in close conjunction with market cycles.
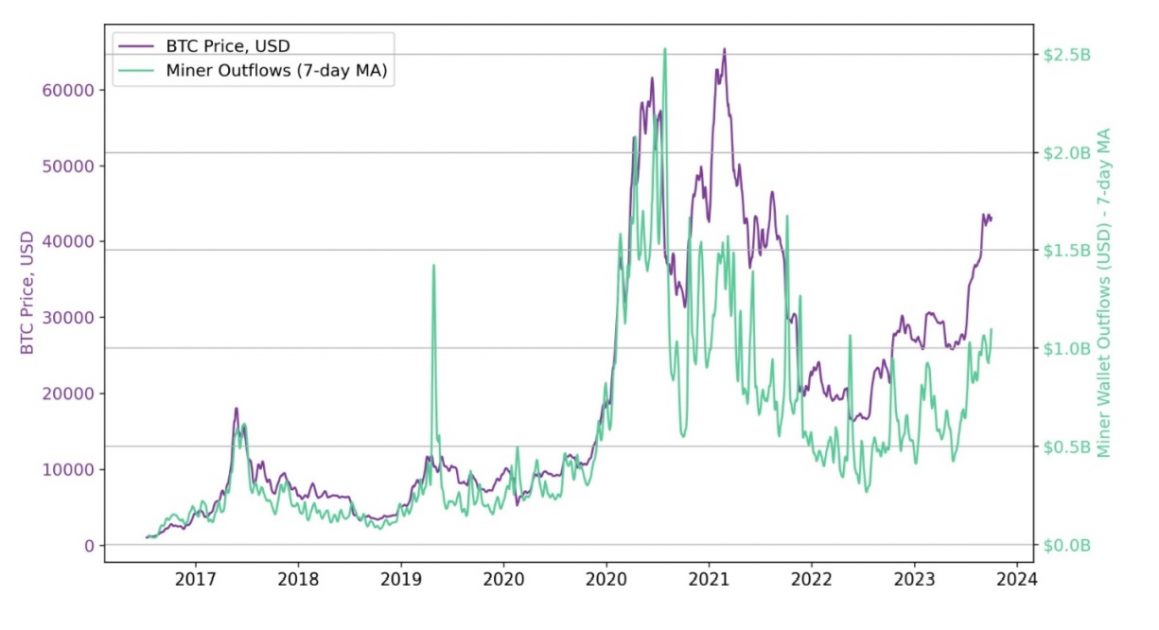
Bitcoin miner breach (1 hop) vs. BTC price (USD), Source: Breaking BFT
The report emphasizes, “This discovery overturns conventional wisdom regarding the relationship between BTC’s deflationary (halving) policy, user fees, and blockchain network security.” “Bitcoin’s security model is supported not only by fee income, but also by miners’ speculative behavior and long-term investment in the network.â€
The speculative behavior and belief in long-term value exhibited by miners is a strong bulwark against the potential security risks facing the Bitcoin network, and this dynamic interplay ensures Bitcoin’s sustainable security. forming a model.
Related: Explaining the advantages of staking and accumulation services and the advantages of virtual currency exchange “SBI VC Tradeâ€
Ignoring profitability and control by the state
There are deeper concerns in the debate surrounding Bitcoin that go beyond simple monetization. In particular, a 51% attack could be carried out continuously if a nation-state attacker targets a blockchain network like Bitcoin and aims to destroy it. However, an attack of this scale would not be able to take advantage of ASIC rental and lending marketplaces.
A scenario in which a nation-state attacker manufactures the ASICs themselves is also envisioned, but given that the S9 model costs approximately $500 per unit, the cost would be more than $20 billion if 40 million units were produced. It is rated as being the best. Additionally, the latest model, the S21, costs about 1/4 of that, including electricity, but problems with the supply network make it less viable.
And while a successful attack could wreak havoc on a network, the community could use techniques like checkpoints and User Activated Soft Forks (USAF) to fight back. These measures help prevent complete destruction of the network even if an attacker is temporarily successful.
Ultimately, the fact that complete destruction is impossible will serve as a deterrent to ideological attacks on networks like Bitcoin. The findings lead the researchers to conclude that “Bitcoin’s security has evolved to the point where the costs and risks associated with attacks far outweigh the potential benefits.â€
Related: Points to note about virtual currency IEOs Domestic and international examples and how to participate
More realistic attack methods
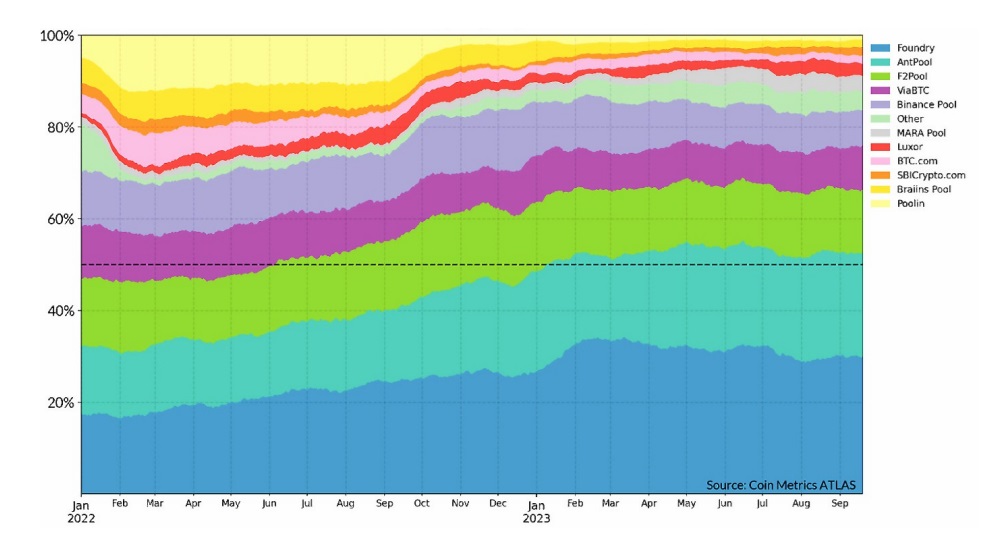
Bitcoin mining pool dominance Source: Breaking BFT
The paper points out the unification of block templates as a more realistic attack method than the 51% attack. Because the entities and algorithms involved in block templating decide which transactions are ultimately recorded on the blockchain, this process creates a concentration of specialized power and creates security risks.
Mining pools are responsible for generating and distributing block templates, but this risks implicit centralization of block templates. The development and introduction of new mining protocols, particularly those like Stratum V2, has the potential to address this issue and reduce the centralization of block templates.
Related: Click here if you want to invest in Bitcoin (BTC)
Half-life special feature
We have introduced the “Heat Map†function to the CoinPost app for investors!
In addition to important news about virtual currencies, you can also see at a glance exchange information such as the dollar yen and price movements of crypto asset-related stocks in the stock market such as Coinbase.â– Click here to download the iOS and Android versions
https://t.co/9g8XugH5JJ pic.twitter.com/bpSk57VDrU— CoinPost (virtual currency media) (@coin_post) December 21, 2023
The post Security outlook after Bitcoin halving: 51% attack is no longer the real risk appeared first on Our Bitcoin News.